
Create a digital signature
There are a variety of online tools that let you create a digital signature. However, it is important to be certain about the software you use to create one. Because in digital signatures, safety is imperative.
Create a digital signature are essentially an algorithm that authenticates the authenticity of digital messages and documents. If the criteria are met, a legally valid digital signature gives the receiver a high-level of confidence that the information was created by a recognized source (authenticity) and that it was not altered during transport (integrity).
Creating a digital signature is a common feature in most cryptographic protocols. They are often utilized for software distribution, financial transactions and contract management systems, and other scenarios where it’s prudent to be cautious about forgery or tampering.
Where are Digital Signatures Used?
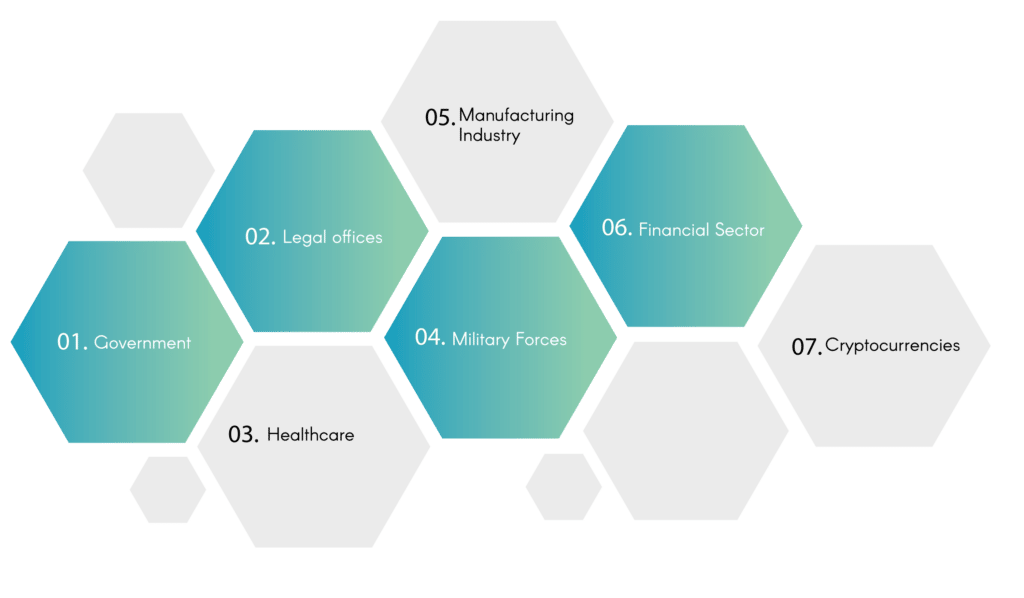
Every day, the impact of digital signatures is becoming more obvious. Many companies have begun using it to increase efficiency while ensuring the integrity of crucial documents. Let’s look at some of the important digital signatures expected to be utilized in 2022.
- Government: Due to its cost-effectiveness and high security, government agencies have begun to utilize digital signs. The government is involved in almost everything, from introducing new laws, tax returns, contract administration, identification cards, and many more. These are all essential documents requiring a digital signature to remove the requirement for a third party to be involved. This makes the process easier and minimizes the possibility of leakage.
- Legal offices: Legal offices are responsible for some of the nation’s most sensitive documents. Digital signatures have drastically reduced the expense of paper and labour. Security of documents is also an issue.
- Healthcare: Creating a digital signature has significantly improved the administration process for health care and treatment.The admissions process is now quicker, and data security has been enhanced.
- Military Forces: The military is among the most crucial and sensitive areas of any nation and has significantly benefitted from the advent of the digital signature. Particularly, security and information compartmentalization has increased 10-fold.
- Manufacturing Industry: To improve the efficiency of the process, manufacturing companies uses digital indicators. This improves the design of products and the quantity of products and sales.
- Financial Sector: The modern-day banking system has reached its peak through paper-free banking, contracts and loans that are quick. Creating a digital signature has made this possible.
- Cryptocurrencies: Cryptocurrencies can be a bit complicated, and blockchain authentication is performed by using create a digital signature. Digital signatures can also be utilized to verify bitcoin transaction details and help determine the ownership.
How to Create a Digital Signature?
You can make or create a digital signature by supplying a one-way hash of the electronic data to be signed by using signing software, for example, an email application.
The term “hash” refers to a fixed-length thread made up of letters and integers created using an algorithm. It is encrypted when it occurs using the digital signature’s originator’s private key. Create a digital signature encrypted hash and other details, such as the hashing technique.
Because a hash function could transform every input to a fixed length result which is typically smaller, encryption of the hash instead of the entire document or message is the preferred method. Hashing is a lot faster than signing, and it can save time.
The value of a hash is unique to the data that it is hashing. A single change in character for an individual string of data can produce a different value. This feature allows other users to recognize the hash using the public key of the signer to confirm the integrity of the data.
It ensures that the information remains the same after it was signed if the decrypted is matches the calculated isolating hash of that identical data. When the hashes do not match, then the data is altered and has been compromised or the create a digital signature has been created using a private key that does not match the public key used to the person signing it, leading to an authentication issue.
The steps needed to create a Digital Signature are described below:
- Go to the eSign site to download Smallpdf;
- Upload the signature-required documents;
- Click on the “Add Signature button to create a signature for the first time;
- Sign your name on your sheet of paper;
- Select ‘Finish and Sign to save the document.
Or, you could make use of different software to sign your documents electronically:
If you’re the sender, you can provide the document for signing in just three steps using eSignature:
- Upload your file to an electronic signing software such as eSignature.
- Then drag the sign, text and date boxes onto the places where the receiver has to act.
- You can send the email. The recipient will receive an email with a hyperlink to the document that they can browse and sign using an electronic create a digital signature software.
If you’re the signer or recipient, then lets you sign your signature in just five steps:
- You can open the email and request that your document be digitally signed.
- Please follow this link. The document should appear online. Create a digital signature software such as eSignature.
- Sign electronically. It is possible to be required to sign documents. After confirmation,
- You will see tags that contain instructions to Sign or Start when the document was signed via electronic signature.
- To include your electronic signature at the time, it is required to sign or initial, simply click on each label and adhere to the directions.
- Check your identity and take your signature on electronic devices by following these steps.
What is PKI?
The Public Key Infrastructure (PKI) is a set of software as well as hardware and processes for managing digital signatures safely. Two keys are utilized in every digital signature process: A public and private key. Everyone who has to confirm the create a digital signature of the signer will be able to access this public key. The private key of the signer isn’t divulged to anyone else and is only used to sign documents electronically.
PKI also requires the use of an authority for certificates (CA) as well as enrollment software and a digital certificate, indispensable management tools, and certificate management.
Conclusion
The public key that is used to sign and create a digital signature is included in a digital certification that identifies the person who is associated with the key. Trusted authorities usually issue digital certificates that are valid for a specified period of time.
The certificate authority serves as the certificate’s security. This blog can help you create digital certificates that include digital signatures online.
FAQ’s
DSC issuance would require 5 business days from the date of applying/application.
A person may have multiple DSCs, but the majority of government websites are required to meet the need to register the DSC on the government server. Once registered, no additional DSC can be used until an additional DSC has been registered.
Electronic signatures are valid for a period of time and have an expiration time of 0 days. Documents that have been signed using electronic signatures using Adobe Sign are certified document that has been sealed with Adobe’s certification.
In the event that you lose your certificate or it gets stolen, the E-Token or I-Key was stolen the person must cancel his certificate and apply for another one. The certificates issued will be valid for 1 year or 2 years, and must be renewed.
